Read more of this story at Slashdot.
Read more of this story at Slashdot.
The chairman of the Federal Trade Commission (FTC) last week sent a letter to Google’s CEO demanding to know why Gmail was blocking messages from Republican senders while allegedly failing to block similar missives supporting Democrats. The letter followed media reports accusing Gmail of disproportionately flagging messages from the GOP fundraising platform WinRed and sending them to the spam folder. But according to experts who track daily spam volumes worldwide, WinRed’s messages are getting blocked more because its methods of blasting email are increasingly way more spammy than that of ActBlue, the fundraising platform for Democrats.
Image: nypost.com
On Aug. 13, The New York Post ran an “exclusive” story titled, “Google caught flagging GOP fundraiser emails as ‘suspicious’ — sending them directly to spam.” The story cited a memo from Targeted Victory – whose clients include the National Republican Senatorial Committee (NRSC), Rep. Steve Scalise and Sen. Marsha Blackburn – which said it observed that the “serious and troubling” trend was still going on as recently as June and July of this year.
“If Gmail is allowed to quietly suppress WinRed links while giving ActBlue a free pass, it will continue to tilt the playing field in ways that voters never see, but campaigns will feel every single day,” the memo reportedly said.
In an August 28 letter to Google CEO Sundar Pichai, FTC Chairman Andrew Ferguson cited the New York Post story and warned that Gmail’s parent Alphabet may be engaging in unfair or deceptive practices.
“Alphabet’s alleged partisan treatment of comparable messages or messengers in Gmail to achieve political objectives may violate both of these prohibitions under the FTC Act,” Ferguson wrote. “And the partisan treatment may cause harm to consumers.”
However, the situation looks very different when you ask spam experts what’s going on with WinRed’s recent messaging campaigns. Atro Tossavainen and Pekka Jalonen are co-founders at Koli-Lõks OÜ, an email intelligence company in Estonia. Koli-Lõks taps into real-time intelligence about daily spam volumes by monitoring large numbers of “spamtraps” — email addresses that are intentionally set up to catch unsolicited emails.
Spamtraps are generally not used for communication or account creation, but instead are created to identify senders exhibiting spammy behavior, such as scraping the Internet for email addresses or buying unmanaged distribution lists. As an email sender, blasting these spamtraps over and over with unsolicited email is the fastest way to ruin your domain’s reputation online. Such activity also virtually ensures that more of your messages are going to start getting listed on spam blocklists that are broadly shared within the global anti-abuse community.
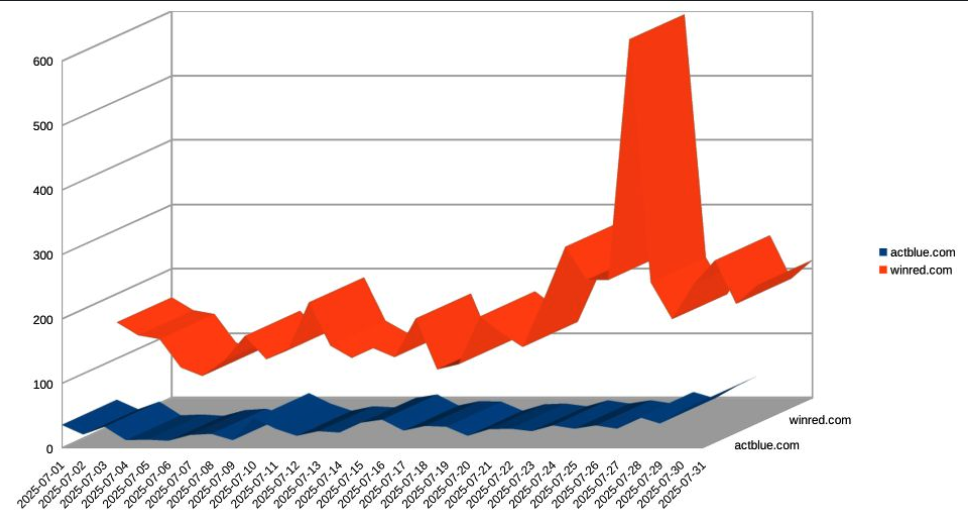
Tossavainen told KrebsOnSecurity that WinRed’s emails hit its spamtraps in the .com, .net, and .org space far more frequently than do fundraising emails sent by ActBlue. Koli-Lõks published a graph of the stark disparity in spamtrap activity for WinRed versus ActBlue, showing a nearly fourfold increase in spamtrap hits from WinRed emails in the final week of July 2025.
“Many of our spamtraps are in repurposed legacy-TLD domains (.com, .org, .net) and therefore could be understood to have been involved with a U.S. entity in their pre-zombie life,” Tossavainen explained in the LinkedIn post.
Raymond Dijkxhoorn is the CEO and a founding member of SURBL, a widely-used blocklist that flags domains and IP addresses known to be used in unsolicited messages, phishing and malware distribution. Dijkxhoorn said their spamtrap data mirrors that of Koli-Lõks, and shows that WinRed has consistently been far more aggressive in sending email than ActBlue.
Dijkxhoorn said the fact that WinRed’s emails so often end up dinging the organization’s sender reputation is not a content issue but rather a technical one.
“On our end we don’t really care if the content is political or trying to sell viagra or penis enlargements,” Dijkxhoorn said. “It’s the mechanics, they should not end up in spamtraps. And that’s the reason the domain reputation is tempered. Not ‘because domain reputation firms have a political agenda.’ We really don’t care about the political situation anywhere. The same as we don’t mind people buying penis enlargements. But when either of those land in spamtraps it will impact sending experience.”
The FTC letter to Google’s CEO also referenced a debunked 2022 study (PDF) by political consultants who found Google caught more Republican emails in spam filters. Techdirt editor Mike Masnick notes that while the 2022 study also found that other email providers caught more Democratic emails as spam, “Republicans laser-focused on Gmail because it fit their victimization narrative better.”
Masnick said GOP lawmakers then filed both lawsuits and complaints with the Federal Election Commission (both of which failed easily), claiming this was somehow an “in-kind contribution” to Democrats.
“This is political posturing designed to keep the White House happy by appearing to ‘do something’ about conservative claims of ‘censorship,'” Masnick wrote of the FTC letter. “The FTC has never policed ‘political bias’ in private companies’ editorial decisions, and for good reason—the First Amendment prohibits exactly this kind of government interference.”
WinRed did not respond to a request for comment.
The WinRed website says it is an online fundraising platform supported by a united front of the Trump campaign, the Republican National Committee (RNC), the NRSC, and the National Republican Congressional Committee (NRCC).
WinRed has recently come under fire for aggressive fundraising via text message as well. In June, 404 Media reported on a lawsuit filed by a family in Utah against the RNC for allegedly bombarding their mobile phones with text messages seeking donations after they’d tried to unsubscribe from the missives dozens of times.
One of the family members said they received 27 such messages from 25 numbers, even after sending 20 stop requests. The plaintiffs in that case allege the texts from WinRed and the RNC “knowingly disregard stop requests and purposefully use different phone numbers to make it impossible to block new messages.”
Dijkxhoorn said WinRed did inquire recently about why some of its assets had been marked as a risk by SURBL, but he said they appeared to have zero interest in investigating the likely causes he offered in reply.
“They only replied with, ‘You are interfering with U.S. elections,'” Dijkxhoorn said, noting that many of SURBL’s spamtrap domains are only publicly listed in the registration records for random domain names.
“They’re at best harvested by themselves but more likely [they] just went and bought lists,” he said. “It’s not like ‘Oh Google is filtering this and not the other,’ the reason isn’t the provider. The reason is the fundraising spammers and the lists they send to.”
A colleague was investigating a crash. The stack at the point of the crash looks like this:
contoso!winrt::impl::consume_Windows_Foundation_Collections_IVectorView<
winrt::Windows::Foundation::Collections::IVectorView<int>,
int>::Size+0x30
contoso!winrt::Contoso::implementation::Widget::
InitializeNodesAsync$_ResumeCoro$1+0x2bc
contoso!wil::details::coro::apartment_resumer::resume_apartment_callback+0x28
combase!CRemoteUnknown::DoCallback+0x34
combase!CRemoteUnknown::DoNonreentrantCallback+0x48
rpcrt4!Invoke+0x64
rpcrt4!InvokeHelper+0x130
rpcrt4!Ndr64StubWorker+0x6cc
rpcrt4!NdrStubCall3+0xdc
combase!CStdStubBuffer_Invoke+0x6c
combase!ObjectMethodExceptionHandlingAction<⟦...⟧>+0x48
combase!DefaultStubInvoke+0x2b8
combase!SyncServerCall::StubInvoke+0x40
combase!StubInvoke+0x170
combase!ServerCall::ContextInvoke+0x3c4
combase!ReentrantSTAInvokeInApartment+0x1fc
combase!ComInvokeWithLockAndIPID+0xcc4
combase!ThreadDispatch+0x514
combase!ThreadWndProc+0x1b4
user32!UserCallWinProcCheckWow+0x180
user32!DispatchMessageWorker+0x130
If we look at the point of the fault:
0:001> r
Last set context:
x0=0000000000000000 x1=00000053af4fdf78 x2=0000017b4f7e6380 x3=0000000000000000
x4=6597e92abf947185 x5=857194bf2ae99765 x6=857194bf2ae99765 x7=0000017b4f700000
x8=00007ff85b11ce40 x9=0000000000000001 x10=0000006700000000 x11=0000000000000000
x12=fffffffffff00000 x13=0000000000000000 x14=0000000000000000 x15=000000000000000b
x16=00007ff8d4fd44a0 x17=ffff68553f08a1c6 x18=00007ff8d0bc0000 x19=0000017b4c834de0
x20=0000000000000000 x21=00007ff8d45cd188 x22=00007ff8d45cd188 x23=00007ff8d45cd150
x24=0000017b31196930 x25=00000053af4fdfa0 x26=00000053af4fe580 x27=0000000000000010
x28=0000000000000000 fp=00000053af4fdf90 lr=00007ff85af448cc sp=00000053af4fdf60
pc=00007ff85af448f0 psr=80001040 N--- EL0
contoso!winrt::impl::consume_Windows_Foundation_Collections_IVectorView<
winrt::Windows::Foundation::Collections::IVectorView<int>,
int>::Size+0x30:
00007ff8`5af448f0 f9400008 ldr x8,[x0]
we see that we are crashing on a null pointer (x0).
The function is a C++/WinRT consume_, which is just a projection of the underlying COM call. The COM call is performed by reading the vtable pointer from the object, reading the function pointer from the vtable, and then calling the function.
The fact that we are reading from x0 (the inbound and outbound parameter slot) means that this is almost certainly reading the vtable pointer from the object: We want the COM pointer in x0 for the outbound call, so the obvious thing to do is to leave it there while you read the vtable pointer from it.
We can confirm this by reading the disassembly.
0:001> u .-30 .
contoso!winrt::impl::consume_Windows_Foundation_Collections_IVectorView<
winrt::Windows::Foundation::Collections::IVectorView<int>,
int>::Size+0x30:
00007ff8`5af448c0 stp fp,lr,[sp,#-0x10]! ; build stack frame
00007ff8`5af448c4 mov fp,sp
00007ff8`5af448c8 bl contoso!__security_push_cookie (00007ff8`5ab91050)
00007ff8`5af448cc sub sp,sp,#0x20
00007ff8`5af448d0 mov w8,#0x1E4
00007ff8`5af448d4 ldr x0,[x0] ; fetch the COM pointer
00007ff8`5af448d8 str wzr,[sp,#0x18]
00007ff8`5af448dc str w8,[sp]
00007ff8`5af448e0 adrp x8,contoso!`string'+0x10 (00007ff8`5b11c000)
00007ff8`5af448e4 add x8,x8,#0xE40
00007ff8`5af448e8 stp x8,xzr,[sp,#8]
00007ff8`5af448ec add x1,sp,#0x18
00007ff8`5af448f0 ldr x8,[x0] ; read the vtable
(The other code is recording the line number and file name for diagnostic purposes.)
Okay, so we are calling IVectorView<T>::Size on a null pointer.
Let’s see whose idea that is.
Here’s the caller:
winrt::IAsyncAction Widget::InitializeNodesAsync()
{
auto lifetime = get_strong();
std::optional<winrt::IVectorView<int32_t>> numbers;
co_await winrt::resume_background();
CallWithRetry([&] {
numbers = GetMagicNumbers();
});
if (numbers == nullptr)
{
co_return;
}
co_await winrt::resume_foreground(m_uithread);
std::vector<winrt::Node> nodes;
nodes.reserve((*numbers).Size()); // ← CRASH HERE
The crash inside consume_ tells us that (*numbers) is null. Let’s see if we can confirm that in the debugger.
First, we have to find numbers.
0:001> dv /V
@x19 @x19 __coro_frame_ptr = 0x0000017b`4c834de0
00000000`00000088 @x25+0x0590 lifetime = struct winrt::com_ptr<
winrt::Contoso::implementation::Widget>
00000000`000000e8 @x25+0x0590 nodes = class std::vector<int>
00000000`000000d8 @x25+0x0590 numbers = class std::optional<winrt::Windows::Foundation::
Collections::IVectorView<int> >
⟦ ... ⟧
The debugger says that numbers is at @x25+0x0590, and that this calculates out to 00000000`000000d8, which is nonsense. So we can’t really trust that calculation.
Let’s see what the code uses. We disassemble backward from the return address.
0:001> k2
Child-SP RetAddr Call Site
00000053`af4fdf60 00007ff8`5b059c8c contoso!winrt::impl::consume_Windows_Foundation_Collections_IVectorView<
winrt::Windows::Foundation::Collections::IVectorView<int>,
int>::Size+0x30
00000053`af4fdfa0 00007ff8`5abc5108 contoso!winrt::Contoso::implementation::Widget::
InitializeNodesAsync$_ResumeCoro$1+0x2bc
We read the return address from the function one deeper on the stack, giving us 00007ff8`5b059c8c.
00007ff8`5b059c84 add x0,x19,#0xD8 // ← setting up the call to consume_
00007ff8`5b059c88 bl contoso!winrt::impl::consume_Windows_Foundation_Collections_IVectorView<
winrt::Windows::Foundation::Collections::IVectorView<int>,
int>::Size
00007ff8`5b059c8c uxtw x1,w0
From the disassembly, we see that the compiler stored the IVector part of the numbers at offset 0xD8 from the coroutine frame, which is in x19.
We can pluck the coroutine frame from the dv output, or we can ask the debugger to restore the nonvolatile registers for us (which includes x19):
0:001> .frame /c 2
0:001> dps @x19+0xd8
0000017b4c834eb8 0000000000000000 // <<<<< the stored IVector 0000017b4c834ec0 0000017b4ff78400
We can ask the debugger for the layout of the std::optional so we can see the full numbers.
I copied the type name from the earlier dv output.
0:001> dt contoso!std::optional<winrt::Windows::Foundation::Collections::IVectorView<int> > +0x000 _Dummy : std::_Nontrivial_dummy_type +0x000 _Value : winrt::Windows::Foundation::Collections::IVectorView<int> +0x008 _Has_value : Bool
Okay, so the value is kept at offset zero, and the _Has_value is at offset 8.
We can eyeball from the earlier dps command that the _Value is nullptr, and the _Has_value is false. (Little-endian means that the single bool is in the least significant byte of the 8-byte value.)
Or we can ask the debugger to interpret it for us.
0:001> dt contoso!std::optional<winrt::Windows::Foundation::Collections::IVectorView<int> > @x19+0xd8 +0x000 _Dummy : std::_Nontrivial_dummy_type +0x000 _Value : winrt::Windows::Foundation::Collections::IVectorView<int> +0x008 _Has_value : 0
Okay, so the numbers has no value.
But wait, our code checked for that!
if (numbers == nullptr)
{
co_return;
}
Why didn’t that work?
Because that’s not how std::optional works.
The std::optional is a sum type of T with a special value called std::nullopt. If you compare a std::optional against anything that isn’t std::nullopt, then you are checking if the std::optional has a value that matches the value you are comparing against.
std::optional holds |
compared with | |
|---|---|---|
std::nullopt |
Y |
|
std::nullopt |
true | false |
X |
false | X == Y |
For the purposes of comparison, an empty std::optional is treated as if it had the value std::nullopt, which is a value distinct from the value values of T.
Therefore, writing if (numbers == nullptr) means “if numbers has a value that is equal to nullptr“.
But in this case, numbers has no value, so the comparison fails, and we fall through.
Then we dereference the *numbers, which is specified to retrieve the wrapped value, and it is undefined behavior if the numbers has no value.
In our case, the numbers indeed has no value, so we have entered the world of undefined behavior. In practice, what happens is that we read whatever is in _Value, and we saw in the debugger, that _Value holds a null pointer. We then try to call Size() on a null pointer and crash.
One fix is to change the test from if (numbers == nullptr) to if (!numbers.has_value()) to ask whether the numbers is empty.
But this is working too hard.
The use of std::optional*<T> was itself unnecessary. There is already a natural empty value for IVector, namely nullptr. So we can declare numbers as an IVector, which default-initializes to nullptr, and then check whether it is still nullptr after we try (and possibly fail) to get a value.
winrt::IAsyncAction Widget::InitializeNodesAsync()
{
auto lifetime = get_strong();
winrt::IVectorView<int32_t> numbers; // remove std::optional
co_await winrt::resume_background();
CallWithRetry([&] {
numbers = GetMagicNumbers();
});
if (numbers == nullptr)
{
co_return;
}
co_await winrt::resume_foreground(m_uithread);
std::vector<winrt::Node> nodes;
nodes.reserve(numbers.Size()); // remove the *
⟦...⟧
This change also covers the case where GetMagicNumbers succeeds but returns a null pointer.
In practice, GetMagicNumbers never returns a null pointer because it knows that the empty set is not the same as no set at all. The original code was testing against something that never happens.
The post The case of the crash on a null pointer even though we checked it for null appeared first on The Old New Thing.
Read more of this story at Slashdot.
A Democrat who was fired from the Federal Trade Commission by President Trump was reinstated to her position yesterday in an appeals court ruling.
Trump's firing of Commissioner Rebecca Kelly Slaughter violated Supreme Court precedent, said yesterday's ruling from the US Court of Appeals for the District of Columbia Circuit. A District Court judge ruled the same way in July, but Slaughter couldn't get back to work because of an administrative stay that delayed the lower-court ruling from taking effect.
The administrative stay was dissolved in yesterday's appeals court ruling, in which a three-judge panel also ruled 2–1 to deny the US government's motion for a longer-term stay pending appeal. "The government has no likelihood of success on appeal given controlling and directly on point Supreme Court precedent," the panel majority said.
The panel pointed to a 1935 case, Humphrey's Executor v. United States, in which the Supreme Court held that the president can only remove FTC commissioners for inefficiency, neglect of duty, or malfeasance in office. Trump's termination notices sent to Slaughter and Democrat Alvaro Bedoya said, "Your continued service on the FTC is inconsistent with my Administration's priorities. Accordingly, I am removing you from office pursuant to my authority under Article II of the Constitution."
In yesterday's ruling, the panel said:
Specifically, ninety years ago, a unanimous Supreme Court upheld the constitutionality of the Federal Trade Commission Act's for-cause removal protection for Federal Trade Commissioners. Over the ensuing decades—and fully informed of the substantial executive power exercised by the Commission—the Supreme Court has repeatedly and expressly left Humphrey's Executor in place, and so precluded Presidents from removing Commissioners at will. Then just four months ago, the Supreme Court stated that adherence to extant precedent like Humphrey's Executor controls in resolving stay motions. To grant a stay would be to defy the Supreme Court's decisions that bind our judgments. That we will not do.
Back to work, FTC Democrat says
The Slaughter case could end up at the Supreme Court. For now, Slaughter wrote that she would be getting back to work this morning.
"Amid the efforts by the Trump admin to illegally abolish independent agencies, incl[uding] the Federal Reserve, I'm glad the court has recognized that he is not above the law," Slaughter wrote last night after the ruling was issued. "I'm eager to get back first thing tomorrow to the work I was entrusted to do on behalf of the American people."
Trump fired Slaughter along with Bedoya in March, leaving the FTC with only Republican commissioners. They both sued the president, but Bedoya subsequently resigned from the FTC to look for other employment. Bedoya's claims were dismissed as moot in July.
The majority in yesterday's 2–1 panel ruling consisted of Judges Patricia Millett and Cornelia Pillard, both Obama appointees. A dissent was filed by Judge Neomi Rao, a Trump appointee.
"I would grant the government's motion for a stay because the government is likely to prevail on the merits of its challenge, and the Supreme Court has reaffirmed that when a court orders reinstatement of an officer removed by the President, the balance of harms favors the government and warrants a stay," Rao wrote.
Rao said she believes "that Humphrey's Executor should be overruled because it is inconsistent with the Constitution's vesting of all executive power in the President and with more recent Supreme Court decisions." She acknowledged "that only the Supreme Court may overrule its precedents" but argued that staying the district court injunction "does not require this court to claim that Humphrey's Executor has been overruled. Instead, the stay is warranted by the Supreme Court's decisions to stay injunctions ordering the reinstatement of removed officers."
Independent agencies and executive power
Although the 1935 Humphrey's Executor ruling was specifically about the FTC, the Trump administration argues that it shouldn't apply to the current version of the FTC because it exercises significant executive power. Rao agrees with that reasoning.
"While leaving Humphrey's Executor in place, the Supreme Court has explicitly recognized that the 'conclusion that the FTC did not exercise executive power has not withstood the test of time,'" Rao wrote. "The Constitution establishes three departments of the federal government, and the so-called independent agencies are necessarily part of the Executive Branch, not some headless fourth branch. Commissioners of the FTC exercise 'considerable executive power,' and such officers are not entitled to reinstatement while they litigate the lawfulness of their removal."
The Supreme Court previously stayed District Court decisions in cases involving Trump's removal of Democrats from the National Labor Relations Board, the Merit Systems Protection Board, and the Consumer Product Safety Commission. In those stay rulings, "the Supreme Court has withheld judgment on the lawfulness of the President's removals of so-called independent agency heads, focusing instead on the harm to the government from reinstatement," Rao wrote. "That reasoning similarly requires a stay here while the merits of the removal, and the ongoing validity of Humphrey's Executor, continue to be litigated."
The majority disagreed with Rao on how to interpret the Supreme Court's recent decisions. Millett and Pillard said that in the National Labor Relations Board case, the stay order included an "admonition that removal protections already upheld by the Supreme Court remain in full effect unless and until the Supreme Court says otherwise." Lower courts should "stay in their lane and leave to the Supreme Court 'the prerogative of overruling its own decisions,'" they wrote.
The majority also concluded that the FTC's powers have not changed since the 1935 ruling. "As the district court well explained, the present-day Commission exercises the same powers that the Court understood it to have in 1935 when Humphrey's Executor was decided," the judges found.